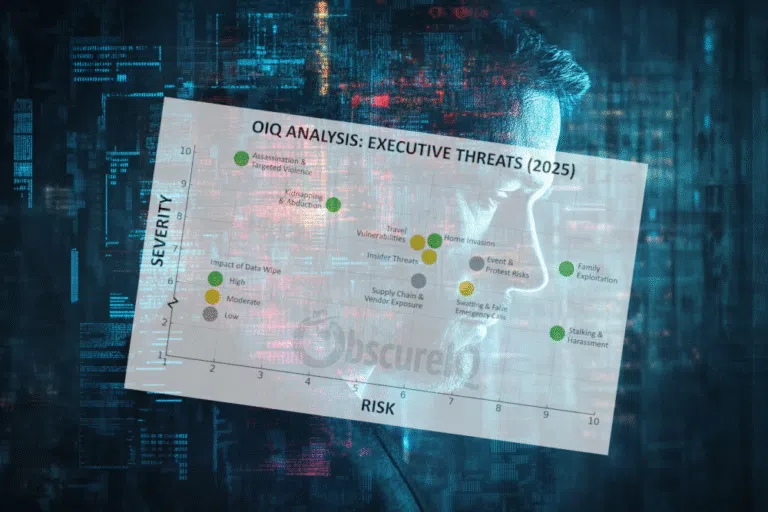
The Top 10 Threats to Executives in 2025
The Top 10 Threats to Executives in 2025: From Boardrooms to Backyards The risks executives face are no longer confined to boardrooms or earnings calls. They emerge from digital exposure, escalate through online chatter, and manifest as physical danger. ObscureIQ’s 2025 Executive Threat Matrix maps the ten most pressing risks. Each one is scored on…