Privacy Posts
Analysis
KYC Is Procedural. Identity Infrastructure Is Structural
March 4, 2026
Why privacy risk lives in the infrastructure layer, not the compliance layer. Most conversations about identity risk begin with KYC…
biometric identity railscompliance enforcement enginescredit bureau identity enrichmentcross domain identity graphscross sector identity linkage
Anonymous Payments
Are Prepaid Credit Cards Anonymous?
March 3, 2026
If You Think a $500 Gift Card Makes You Invisible, You’re 20 Years Behind. There is a persistent belief that…
AML reporting thresholdsanonymous paymentsbilling ZIP registration riskconsumer payment privacy hygienedevice fingerprinting
OSINT & Intelligence Analysis
Domain Purchases and Decisions Reveal More Than You Think
February 24, 2026
Most people think a domain is just a name. Not true. A domain is the front door to a stack…
analytics tracking identifierscertificate transparency logsdigital residueDNS recordsdomain intelligence
AI
Domain Intelligence Is No Longer About Domains
February 19, 2026
How Consolidation Rewired the Risk Layer in 2026 Domain intelligence is no longer a security discipline.It is a financial asset…
adversary infrastructure trackingattribution model collapsecontrol plane analysisdomain intelligence consolidationdomain intelligence taxonomy
Credible Threats
Blocking Feels Safe. It Isn’t.
February 17, 2026
Why Removing a Harasser From One Channel Doesn’t Remove Your Exposure. You block the number. Or the account. Or the…
blocking is not protectioncontact surface reductiondata broker harassmentdigital exposure riskdigital threat escalation
Data Brokers
How to Stop Data Brokers from Selling Your Personal Information
February 12, 2026
A Tactical Framework for High-Risk Individuals They collect it. Standardize it. Enrich it. Resell it. Then repackage it again. If…
affiliate data resellersanti correlation strategybroker relisting preventioncommercial-surveillancecorrelation density
Identity Intelligence
Attackers Don’t Hack You. They Know You.
February 5, 2026
Attackers Don’t Hack You. They Know You. Most phishing and social engineering discussions focus on tactics. Better filters. Better training.…
adversarial researchattack surface mappingcontextual attacksdata aggregationData brokers
Commercial Surveillance
Crumbs for a Crown
January 30, 2026
The Quiet Deal We All Make With Big Tech The Quiet Deal We All Make With Big Tech A year…
AI and data reusebehavioral databig tech surveillanceconsent theaterdata aggregation
Digital Footprint
Domain History Is Forever
January 23, 2026
Domain History Is Forever. Plan Accordingly. Registering a domain is a disclosure event. It is not a private act. You…
attack surface mappingattribution riskdata aggregationdigital footprintdomain correlation
Data Breach
When Your Personal Data Is Exposed…
January 20, 2026
A Data Breach Triage Guide for Real-World Risk Non-negotiable baseline If credentials, recovery paths, or government identifiers are exposed,…
account takeover preventionadversary researchbreach monitoringbreach triagecredential reuse
Adversarial Research
Boutique Intelligence vs. Big Providers
January 14, 2026
Boutique Intelligence vs. Big Providers: Why Smaller Is Safer for High-Risk Decisions When you’re facing a high-risk decision – a…
alpha groupasset tracingbespoke investigationsboutique intelligencecorporate investigations
Attack Surface Mapping
OSINT + HUMINT
January 14, 2026
The Missing Link in Modern Due Diligence In 2025, nobody makes a serious decision without some kind of due diligence.…
alpha groupbackground checkscompliance verificationcorporate investigationscross-border M&A
AI
Gmail Is No Longer a Neutral Tool
January 7, 2026
A quiet shift high-risk people should not ignore Gmail used to be a tradeoff.Less privacy. More convenience. That balance is…
AI in email platformsEmail content scanningEmail data retentionEmail threat surfaceExecutive communication security
Biometric Identifiers
When the Internet Demands Your Identity
January 6, 2026
Your Identity Is Becoming the Price of Entry The web is changing fast. Governments are pushing identity checks deeper into…
Biometric data collectionData minimization principlesDigital identity exposureFacial recognition privacyGovernment ID checks
Communication Privacy
The 6–7 Privacy Stack
December 31, 2025
Real Protection Without Breaking How You Work. Most privacy advice fails because it assumes perfect behavior. Executives do not have…
Cloud SecurityDigital Privacy ToolsEncrypted Emailexecutive privacyPassword Management
Communication Privacy
Why You’re Getting Fake Calendar Invites (And Why They’re Dangerous)
December 22, 2025
How high-profile individuals are now being targeted through their calendars Your calendar is no longer just a scheduling tool. It…
calendar phishingcalendar security riskscredential harvestingdigital footprint exposureexecutive security threats
Commercial Surveillance
The DRIVER Act Drives Privacy Into a Ditch
December 19, 2025
How a Right-to-Repair Bill Quietly Expands Vehicle Data Exposure Modern vehicles generate constant data. Where you go. When you stop.…
automobile surveillanceautomotive data brokerscommercial surveillance risksconnected car dataconsent theater in privacy laws
AI
The Power of Dumb AI
December 18, 2025
Read This Before You Argue About AGI What Fiction Gets Right About AI Risk Without Sentience Most people picture AI…
AI risk analysisautomation at scalehuman oversight failureslarge language modelsmisaligned incentives
Communication Privacy
Secure Messaging Is Not One Problem
December 16, 2025
Secure Messaging Is Not One Problem The Real Question Is: Who Are You Hiding From? Most people choose a messaging…
anonymous messagingcommunication privacyencryption tradeoffsmetadata exposuresecure messaging
Analysis
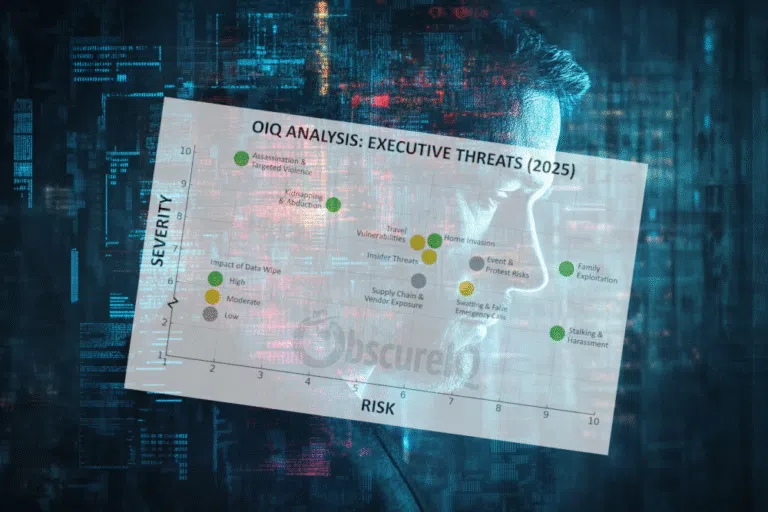
The Top 10 Threats to Executives in 2025
December 10, 2025
The Top 10 Threats to Executives in 2025: From Boardrooms to Backyards The risks executives face are no longer confined…
assassination risksfamily exploitationhome invasioninsider threatskidnapping threats
Analysis
Three Truths of Cyberphysical Attacks
December 5, 2025
Three Truths of Cyberphysical Attacks The future is not digital or physical. It is both. Attackers already understand this. Three…
automation as weaponcyberphysical attacksdigital to physical threatsdrone harassmenthigh-profile targeting
Surveillance Evasion
A VPN Ban Won’t Protect Kids
December 1, 2025
A VPN Ban Won’t Protect Kids (But It Will Break Everything Else) Age verification laws tied to VPN bans are…
age verification lawschild online safetycorporate vpn securitydigital privacyinternet censorship
Anonymous Payments
Shop Quietly
November 27, 2025
Reduce Your Digital Footprint and Take Control Every Time You Checkout Online shopping simplifies life. It also exposes large amounts…
anonymous paymentsData brokersdigital footprintmasked emailonline shopping privacy
Anonymous Payments
The Strategic Guide to Virtual Credit Cards
November 14, 2025
Why VCCs Don’t Grant Anonymity. And How to Use Them for Maximum Compartmentalization and Breach Protection Virtual credit cards (VCCs)…
apple paycapital one enociti vanscompartmentalized paymentsfinancial data protection
Financial Privacy
Privacy Isn’t Dead :: You’re Just Doing It Wrong
November 12, 2025
Three Easy Actions That Actually Protect Your Personal Data Privacy advice can get overwhelming. Most people don’t know where to…
Browser privacycommunication privacyData brokersDe-GoogledFinancial privacy
Analysis
Weaponized Purpose: How Data Collected to Help Us Becomes Data Used Against Us
November 10, 2025
Data starts with intent. It’s collected to protect, connect, and improve our lives. But once shared, that same data moves…
behavioral scoringbreach exploitationidentity graphintended purposemovement data
Analysis
When Your Domain Gets Hijacked
October 31, 2025
The Danger of the Expired Domain Name Most hijacked domains aren’t hacked at all. They’re abandoned. And then weaponized. A…
acpaai domain auctionsdns/ms auditdomain expirationdomain hijacking
Analysis
Biometric Trap: When Your Body Becomes the Leak
October 27, 2025
Biometric Trap: When Your Body Becomes the Leak What if a threat actor could strap you to a brain scanner…
active threat monitoringbiometric databasesbiometric exploitationbiometric intelligencebrainwave monitoring
Analysis
Biometric Identifiers Executives Can’t Ignore
October 24, 2025
Biometric Identifiers Executives Can’t Ignore Executives and high-net-worth individuals already live under constant exposure: financial leaks, digital footprints, and physical…
ai voice cloningbiometric authenticationbiometric risksbiometric surveillanceborder biometrics
AI
Which Generative AI Is Most Privacy-Respecting?
October 22, 2025
Does Your Chatbot Spy on You? ObscureIQ | 2025 Edition Artificial intelligence is now part of daily life. Drafting documents.…
ai privacy rankingclaude privacy settingscloud aidata retentiondigital footprint reduction
Analysis
The Executive Threat Matrix: How Data Wipes Shift the Risk
October 17, 2025
The Executive Threat Matrix: How Data Wipes Shift the Risk Executives face ten major categories of threat in 2025. Each…
data-suppressiondata-wipesdigital footprintfamily exploitationfootprint erasure
Commercial Surveillance
AR Glasses: A New Threat Surface for High-Value Targets
October 9, 2025
AR Glasses: The Surveillance Tool Disguised as Fashion Augmented reality (AR) glasses are not just eyewear. They’re surveillance tools disguised…
ar eyewearar glassesbiometric datacorporate espionagedata wholesalers
Commercial Surveillance
Argyle and the New Data Grab Disguised as Verification
September 30, 2025
Argyle and the New Data Grab Disguised as Verification A landlord demanding Argyle verification isn’t just a rental issue. It’s…
argyle.comcheckrconsumer consentcredential harvestingemployment verification
Assets & Identity
The Hidden Market in DMV Records
September 25, 2025
The Hidden Market in DMV Records How state agencies feed data brokers. And how scammers exploit the fallout. You’ve probably…
consumer exposuredata resaledmv datadmv recordsdownstream data sharing
Assets & Identity
Meta’s Neural Band + Future Biometric Identifiers
September 20, 2025
Meta’s Neural Band + Future Biometric Identifiers This week, Meta unveiled its Ray-Ban Display glasses paired with a Neural Band…
brain computer interfacecognitive biometricselectromyographyfuture of surveillancegesture biometrics
Comparison Guide
Left Behind by Windows 11? Safe Alternatives
September 17, 2025
Microsoft’s decision to limit Windows 11 to newer hardware has left millions of PCs behind. If you’re running an older…
chromeos flexdebianfedorafreebsdlinux for privacy
ALPR
Opinion: Flock Safety is Surveillance Sold as Safety
September 17, 2025
Opinion: Flock Safety is Surveillance Sold as Safety Garrett Langley, CEO of Flock Safety, wants the world to believe his…
civil libertiescommercial-surveillancefear-driven surveillanceflock safetylicense plate readers
ALPR
When a License Plate Becomes a Target
September 8, 2025
When a License Plate Becomes a Target How High-Profile Individuals Can Be Tracked Using ALPR Networks ALPR systems weren’t built…
drn dataflock safetypaparazzi-monitoringprotest-surveillancesurveillance risk
Analysis
How Spyware Operators Like NSO Win and How to Defend Yourself
September 8, 2025
How Spyware Operators Like NSO Group Win(and How to Defend Yourself) Spyware operators like NSO Group, creators of Pegasus, are…
cloud exposureforensic-scannso grouppegasusphone security
Adtech
ALPR vs. GPS: Why License Plate Tracking Is Surging
September 8, 2025
ALPR vs. GPS: Why License Plate Tracking Is Surging Law enforcement has always had ways to follow you. Phones broadcast…
drnflock safetygpshoasice
Analysis
Why Deepfakes Are Harder to Stop Than We Admit
September 4, 2025
I mapped dozens of proposed solutions to deepfakes. The result was sobering:No silver bullets. Only tradeoffs. The conversation around deepfakes…
deepfake detectorgovernment regulationprovenance toolsrapid takedownstech ban
Analysis
The CSI Enhance Button Is a Lie: What Image Al Really Does
September 3, 2025
The CSI Enhance Button Is a Lie: What Image Al Really DoesPop culture has trained us to believe in a…
adobe fireflyai upscalingcsideep learningdiffusion models
Adtech
Ghost in the Pixels: How Hidden Image Payloads Target AI Users
September 3, 2025
Ghost in the Pixels: How Hidden Image Payloads Target AI Users Recent research from Trail of Bits shows how attackers…
aiai securityanamorphercomputer visioncybersecurity
Adtech
Politi-Spam: Apple, Gmail, and the Data Broker Machine
September 3, 2025
Politi-Spam: Apple, Gmail, and the Data Broker Machine Your phone shouldn’t be a campaign donation funnel. Apple just agreed. In…
actblueacxiomappleftcgmail
Credible Threats
Lock Down Browsers. Wipe Employee Footprints. Win Breach Wars.
September 2, 2025
Lock Down Browsers. Wipe Employee Footprints. Win Breach Wars. Over 80% of security incidents now start in the browser. Chrome.…
brave browserbreachesbrowser exploitbrowserschrome
Financial Privacy
Buy Property in a Trust. Or Regret It Later: A Tactical Guide to Real Estate Ownership That Actually Protects You
August 7, 2025
By Greg Manwelyan, for readers who understand anonymity isn’t a luxury, it’s a necessity Let’s be blunt: buying real estate…
anonymityasset protectioncreditorsdeedliving trust
Financial Privacy
The Best State for Your Real Estate LLC Isn’t Where You Think It Is
August 3, 2025
By Greg Manwelyan, for privacy‑conscious operators who understand that real estate ownership shouldn’t equal public exposure Forming an LLC in…
anonymous llcasset protectiondelawarenew mexiconominee manager
Financial Privacy
Trust + LLC Layering: The Real Estate Ownership Strategy That Actually Works
August 1, 2025
By Greg Manwelyan, for readers who know that real privacy starts where the public record ends Owning real estate is…
anonymous llclayeringnominee managerprivate mailboxrevocable living trust
ALPR
A Day in the Life of Your License Plate
July 28, 2025
How ALPR Systems Quietly Track You Everywhere Your License plate is talking more than a drunk uncle at Thanksgiving. Automatic…
atlas of surveillanceconduentdeflockdrnflock safety
ALPR
Your License Plate is Talking… Who’s Listening?
July 26, 2025
Your plates used to talk to the DMV and the occasional traffic cop. In 2025? They’re snitching to data brokers,…
alprapartment complexesautomatic license plate recognitioncyberstalkinggated communities
ALPR
Your License Plate Is a Beacon: How Everyday Driving Becomes a Surveillance Trail
July 25, 2025
Automatic License Plate Recognition (ALPR) systems have created a shadow network of tracking that spans across cities, highways, and even…
alprautomatic license plate recognitioncorporate espionagegated communitylaw enforcement
Analysis
Password Managers: Privacy, Anonymity, and Security
July 24, 2025
🔹Top Picks at a Glance From our latest analysis, here’s how some of the most popular password managers performed: Bitwarden…
1passwordbitwardendashlanekeepassnordpass
Analysis
Anonymous Phones in 2025: Getting Out of the Apple and Google Trap
July 23, 2025
When it comes to reducing your digital exposure, few steps are as impactful as getting out of a stock phone.…
above-phonebittium-tough-mobile-2ccalyxosgrapheneoskatim r01
Assets & Identity
How Data Brokers Destroyed Functional Privacy
July 22, 2025
There was a time, not so long ago, when we had something called functional privacy. Not perfect privacy. Not encryption.…
court databasesdaniel’s lawerase recordsindexed searchable soldmonetized loopholes
Threats & Exploits
Are Human Therapists Causing Suicides? No. (And perhaps AI therapists are not either.)
July 22, 2025
About 12,000 people die by suicide each year while actively in therapy with a licensed professional. [Psych Today] Nobody blames…
aiai guardrailssuicidetherapy
Analysis
Credit Headers: The Unseen Data Firehose
July 19, 2025
Your personal data isn’t just sitting in a credit bureau vault. It’s being actively spread across the internet through a…
credit bureauscredit headersequifaxexperiantransunion
De-Googled
How to Remove Your Home from Maps
July 15, 2025
Mapping software is showing your home to everyone—even bad actors. Be Safe! If images of your home appear on mapping…
apple mapsbing mapsblur homegoogle mapsmap data
Credit
What Is Credit Monitoring? And Do I Want It? (Answer: Not Really)
July 14, 2025
Every time there’s a major data breach, companies scramble to offer “free” credit monitoring. It sounds like a responsible move.…
breach economycredit freezecredit scoreequifaxexperian
Adtech
Maximize Facebook Privacy
July 12, 2025
Everyone wants your location—because it’s valuable. Lock it down! Your privacy on Facebook matters. Whether you’re concerned about who can…
ad preferencesface recognitionfriend listsfriend requestslocation services
Uncategorized
Safe Surf Risky Content
July 11, 2025
Everyone wants to track you and hack you. Don’t surf without protection! Whether you’re an investigator, law enforcement officer, or…
Data Brokers
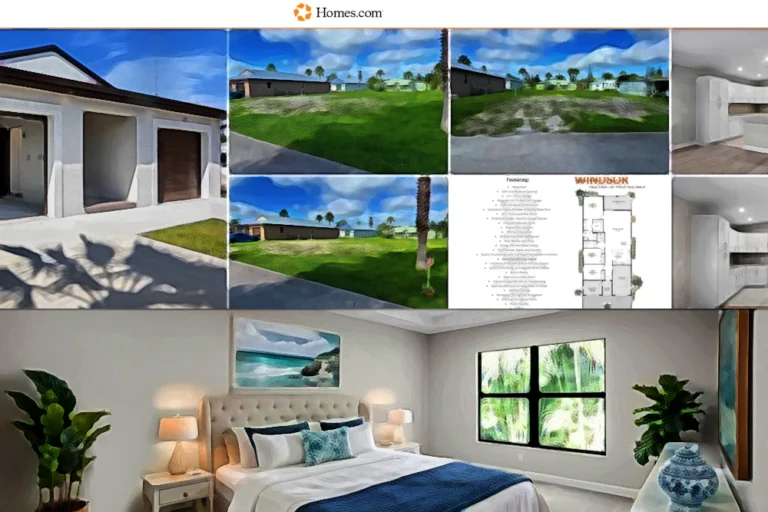
Remove Residential Data
July 10, 2025
Don’t let everyone see pictures of your home! Real estate sites often show images that reveal far more than you…
floor planhomes.cominterior photosproperty imagesproperty records
Location Privacy
Find Your Mobile Ad ID
July 9, 2025
Your Mobile Advertising ID (MAID) is the key to deleting your location history. You are being tracked. Advertisers and data…
adjust insightsappsflyergaidgoogle advertising ididentifier for advertisers
Uncategorized
Secure Private URL Reg
July 8, 2025
Secure Private URL Registration: Protect Your Identity Online Registering a domain without protecting your personal information is risky. Domain registrars…
Uncategorized
The Sextortion Scammers’ Process
July 7, 2025
How scammers trick you into thinking they know something revealing… Don’t be fooled! They don’t actually know you, and they…
Assets & Identity
Be Location Safe
July 5, 2025
Be Location Safe (Aug 2025) Everyone wants your location. It’s valuable.Don’t let companies harvest and sell your geolocation data. They…
ad trackingairplane modeapp trackinggoogle mapslocation history
Credible Threats
Signals in Plain Sight (Covert Communication Channels)
July 4, 2025
At ObscureIQ, we’re rolling out ThreatWatch. It’s our new active threat monitoring service. Looking for threats forces us to think…
emoji substitutionshidden messagesin-game chatmod-based signalingsteganography
Analysis
5 Privacy Moves to Block Spies, Trackers, & Data Brokers
July 3, 2025
Stalkers, advertisers, and hostile actors are digging for your data every day. Your phone is revealing your location. Your credit…
chromecredit freezelocation trackingpassword managerprivacy-first phone
Comparison Guide
Secure Messaging in 2025: What You Need to Know
June 28, 2025
Secure Messaging in 2025: What You Need to Know Messaging isn’t just conversation. It’s exposure. The app you use determines…
chatmatrixsecure messagingsessionsignal
Anonymous Payments
Prepaid Gift Card Chart for Private Payments
June 25, 2025
When you want to make online payments without leaving a clear personal trail, prepaid cards can be powerful tools. But…
amex servebitpay prepaidcrypto.comgift cardsmastercard prepaid
Comparison Guide
Anonymous Email Services
June 23, 2025
Tactical Privacy: Email Address Strategy The longer you hold onto an email address, the more data brokers can cluster around…
guerrilla mailmailbox.orgproton mailsimpleloginstartmail
Anonymous Phones
Buying Guide to Used Phones
June 18, 2025
What You Need to Know Most phones are built to track you. Carriers want your ID, platforms want your accounts,…
activation lockburner phone setupdevice integrity checksfactory resetimei
Comparison Guide
Best Encrypted Cloud Storage
June 17, 2025
The Truth About Encrypted Cloud Storage: Which Option Protects You Best? Cloud storage has become unavoidable. Every document, photo, and…
anonymitybigtechcloud storageencryptionproton drive
Device Hardening
Letting AI Summarize Unknown Email, Docs
June 15, 2025
Letting AI Summarize Unknown Email, Docs… Gives attackers a way to execute hidden commands. Your “summary” is their payload. AI…
ai exploitgeminigmailphishingprompt injection
Tools & Defenses
Best Browsers for Privacy (2025)
June 14, 2025
OIQ Briefing: Best Browsers for Privacy (2025) Your browser is your first line of defense online. Pick the wrong one,…
anti-trackingbrowser securityduckduckgolibrewolfprivacy browser
Analysis
Brokers & Doxxers: From Exposure to Exploitation
June 11, 2025
Brokers & Doxxers: From Exposure to Exploitation Every week we hear from clients who discover their address, phone number, or…
anti-doxxingcybercrimeexploitationexposureharrassment
Anonymous Payments
Getting Your Money When You’re Off the Grid
June 2, 2025
Let’s say you had to run. Maybe you’re a whistleblower. Or maybe you crossed someone powerful. You’re out of the…
amexcapital oneencryptionfintechforeign llc
Analysis
Sextortion Spam
May 10, 2025
Sextortion scams aren’t new, but they remain one of the most effective forms of cyber-enabled fraud. These scams don’t rely…
bitcoindeadlinefeargoogle maps apiransom