The Executive Threat Matrix: How Data Wipes Shift the Risk
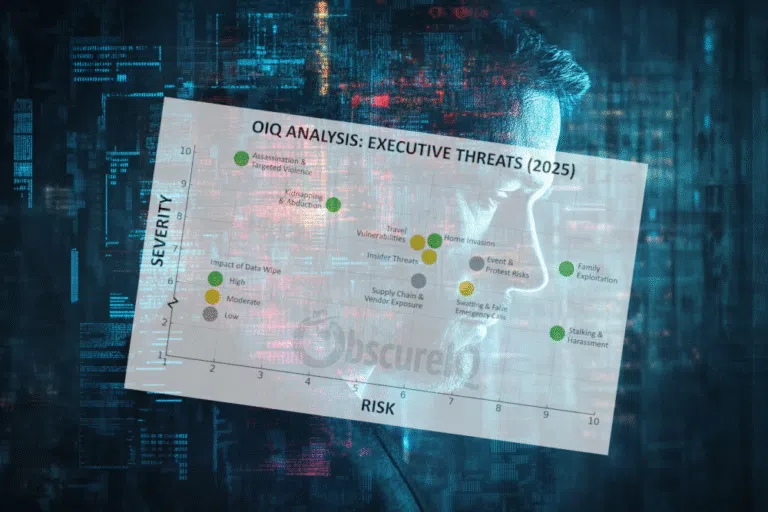
The Executive Threat Matrix: How Data Wipes Shift the Risk Executives face ten major categories of threat in 2025. Each carries a different blend of risk — how often it happens — and severity — how damaging it is when it does. The chart below from ObscureIQ’s Executive Threat Matrix makes one truth unmistakable: most…