The Executive Threat Matrix: How Data Wipes Shift the Risk
Executives face ten major categories of threat in 2025. Each carries a different blend of risk — how often it happens — and severity — how damaging it is when it does.
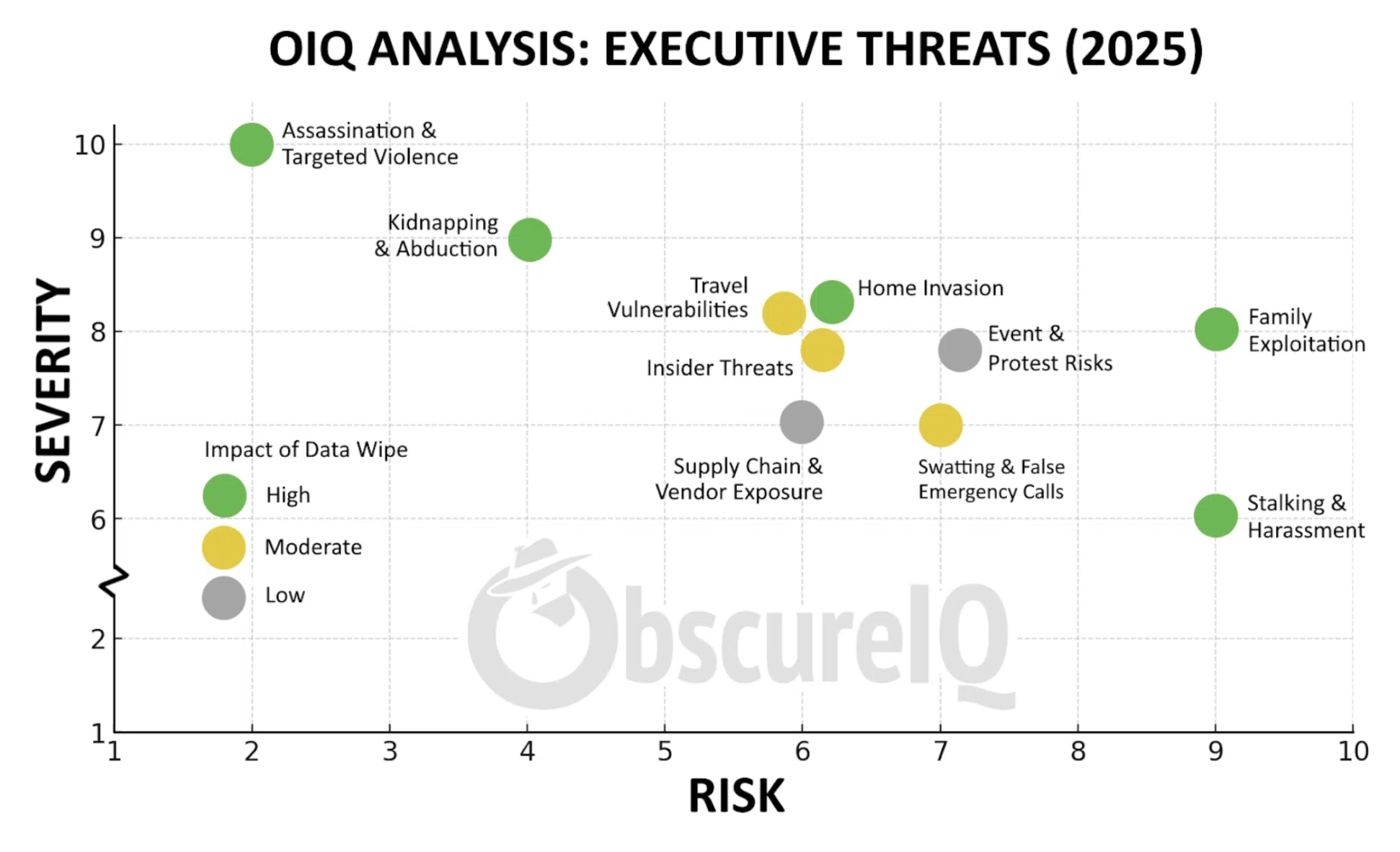
The chart below from ObscureIQ’s Executive Threat Matrix makes one truth unmistakable: most of these pathways begin with exposed digital data. Home addresses, school listings, travel itineraries, even relatives’ social posts — these fragments are the breadcrumbs adversaries stitch into an attack map.
And here’s the insight that matters most: the highest-severity and highest-risk threats on the board are also the ones most reduced by data wipes. Assassination attempts, kidnappings, family exploitation, and stalking all rely heavily on digital exposure. Remove the breadcrumbs, and the attack pathways collapse.
Where Data Wipes Have the Biggest Impact
- Assassination & Targeted Violence — Suppressing home addresses and itineraries removes the most common targeting vectors.
- Home Invasion — Property record suppression directly shrinks the attack surface.
- Kidnapping & Abduction — Erasing school and family travel leaks closes planning routes adversaries rely on.
- Stalking & Harassment — Rapid doxxing takedowns cut off harassment channels before escalation.
- Family Exploitation — Family-focused suppression is critical. Attackers often pivot to spouses and children when the principal is hardened.
Moderate and Low Impact Areas
Some threats can only be reduced, not erased. See our guidance on threat mitigation for tactics addressing spoofing and other escalation methods. Travel exposure often comes from public disclosures. Events are public by design. And vendor oversharing is frequently outside an executive’s direct control.
ObscureIQ Insight
The chart shows it plainly: data suppression is not theory — it’s leverage. The most severe and most common threats are also the most preventable through digital footprint erasure.
Erase the map. Reduce the risk.