Biometric Identifiers Executives Can’t Ignore
Executives and high-net-worth individuals already live under constant exposure: financial leaks, digital footprints, and physical security threats. But a new layer is emerging that cuts deeper than devices or passwords: biometric identifiers.
Your face, your DNA, your voice. Even your subconscious brain activity. Are now being captured, analyzed, and stored. Unlike a compromised password, these identifiers can’t be reset. Once collected, they follow you for life.
That’s why ObscureIQ has produced a focused analysis of biometric threats most relevant to executives. [Download the full PDF here.]
Unavoidable Everyday Exposures
Some biometrics are already woven into daily life. These systems are difficult (or impossible) to opt out of:
Facial Recognition
Embedded in airports, retail, law enforcement, and consumer devices. Tracks individuals passively and at scale.
Fingerprint Recognition
Ubiquitous on smartphones and access systems. Highly reliable, but vulnerable to spoofing and coercive unlocks.
Voice Recognition
Used in call centers, finance, and telecom. Convenient for authentication but easily exploited with AI voice cloning.
These identifiers represent permanent exposures: if you live or work in the modern world, you’re already being scanned.
Checkpoint & Coercive Collection
Other biometrics aren’t collected passively but are increasingly required at borders, secure facilities, or high-security environments. Refusal isn’t an option:
Iris Recognition – Widely deployed at airports and secure facilities. Nearly impossible to fake and often mandated for access.
Retina Recognition – Extremely accurate, but requires close-range, intrusive imaging. More niche, but offers adversaries absolute certainty of identity.
DNA Sampling – Permanent, irrevocable, and tied to family. Collection at borders, labs, or health settings creates risks that extend across generations.
Hand Vein Recognition – Adopted in banking and secure access systems. Hard to spoof, but can be coercively harvested.
These systems are most likely to be forced onto executives during international travel or controlled facility entry.
Psychological Exploits
The most destabilizing risks aren’t physical at all. They target the mind and emotions:
Brain Imaging / Brainwave Signatures – Reveal subconscious thoughts, health conditions, or stress states. Useful in medicine but catastrophic if weaponized.
Emotional AI & Micro-expression Analysis – Claim to read hidden emotions or intentions. Risk of manipulation in negotiations, interrogations, or political profiling.
These technologies are less common today, but they represent the future battleground of biometric exploitation.
Why It Matters for Executives
Unblockable Risks – Face, fingerprints, and voice are unavoidable. Executives must assume exposure.
Travel Chokepoints – Iris, retina, DNA, and vein recognition are most likely to be collected when moving across borders or entering secure facilities.
Weaponization Potential – DNA, brain signals, and emotional analytics can be turned into tools of blackmail, coercion, or reputational attack.
Strategic Implications
Unblockable Risks: Face, iris, DNA, and voice are virtually impossible for clients to avoid without radical lifestyle shifts. These should be the primary education points.
Psychological Exploits: Brain- and emotion-based biometrics represent an underappreciated frontier—executives should be warned now, before adoption scales.
Travel/Checkpoint Pressure Points: Iris and retina recognition, plus DNA sampling, are most likely to be forced during international movement. That makes executives especially vulnerable when traveling abroad.
Weaponization Potential: DNA, brain signals, and emotional AI are the most ripe for coercion, blackmail, or reputational targeting.
⚠️ Related Threat Intelligence
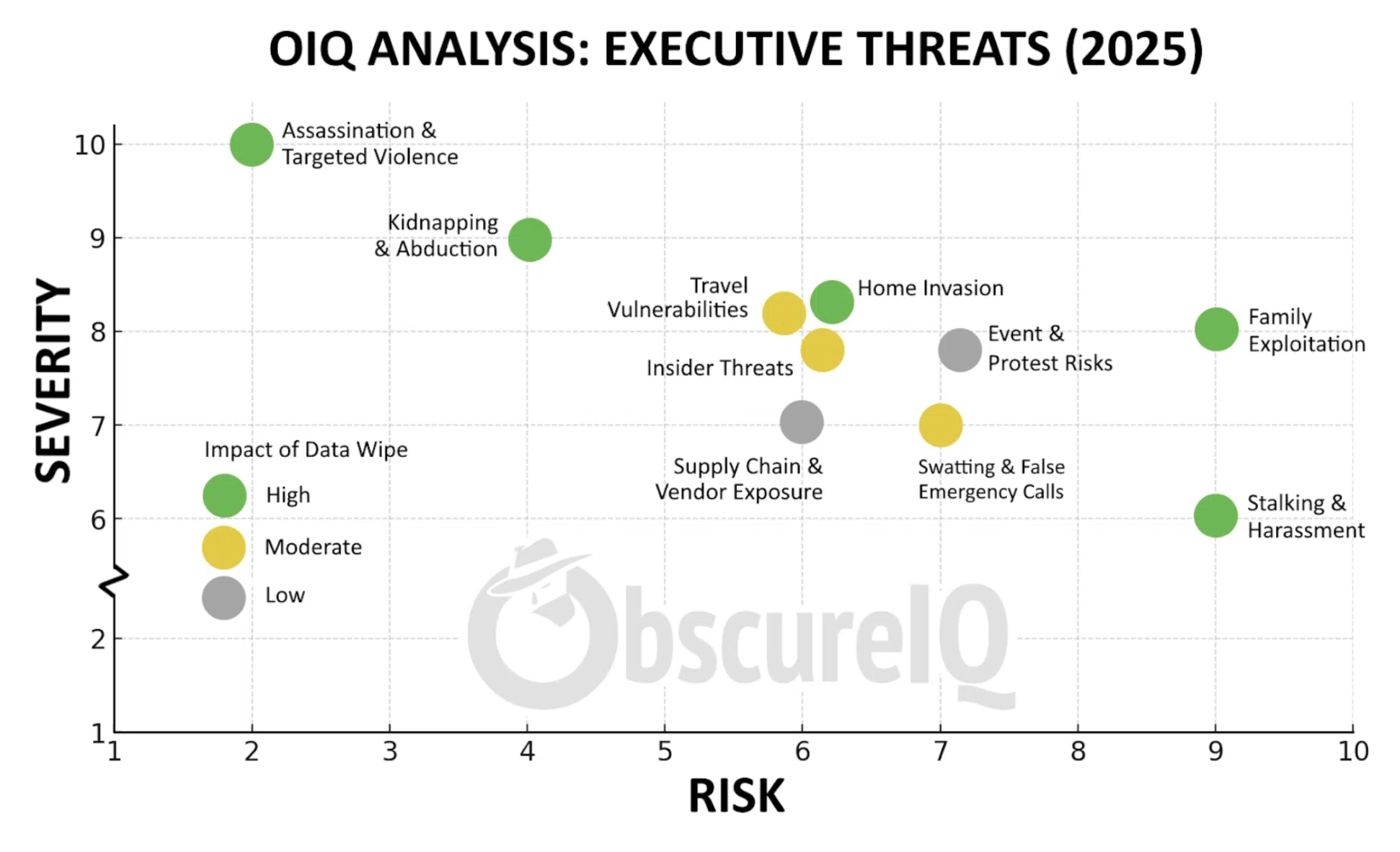
📊 The Executive Threat Matrix: How Data Wipes Shift the Risk
Understanding how digital exposure affects executive risk requires a comprehensive framework. Our Executive Threat Matrix maps the relationship between data visibility and threat probability across different attack vectors.
Learn more about emerging threats to executive privacy:
Where ObscureIQ Fits
Our role is twofold: to map this emerging biometric threat surface and to help executives prepare for its inevitable exploitation.
The ExecThreats analysis identifies the ten biometric identifiers with the highest adversary value and the lowest chance of avoidance.
📄 [Download the PDF now]
Protection Services for High-Risk Profiles
ObscureIQ provides comprehensive protection for executives facing advanced threats:
- Digital Footprint Wipe – Remove exposed personal data from data brokers and public records
- Active Threat Monitoring – Real-time alerts for emerging risks to your identity
- Circle of Risk Investigations – Assess vulnerabilities across family, staff, and associates
- Threat Actor Unmasking – Identify and expose adversaries targeting your organization
- Organizational Assessment – Identify privacy gaps in your company’s operations
Additional Privacy Resources
Strengthen your privacy posture with our comprehensive guides:
Identity Protection:
Privacy Tools & Technologies:
Physical & Asset Privacy:
The biometric era is here. The question isn’t whether your data will be collected—it’s who controls it, and what they’ll do with it.
Learn more about Protection for Organizations or explore our Privacy Guides to take control of your digital exposure.