Data starts with intent. It’s collected to protect, connect, and improve our lives. But once shared, that same data moves through brokers, algorithms, and surveillance systems. Adapting to new incentives.
Weaponized Purpose reveals how twelve common data categories evolve from helpful to harmful, showing the real-world systems that turn ordinary information into instruments of control.
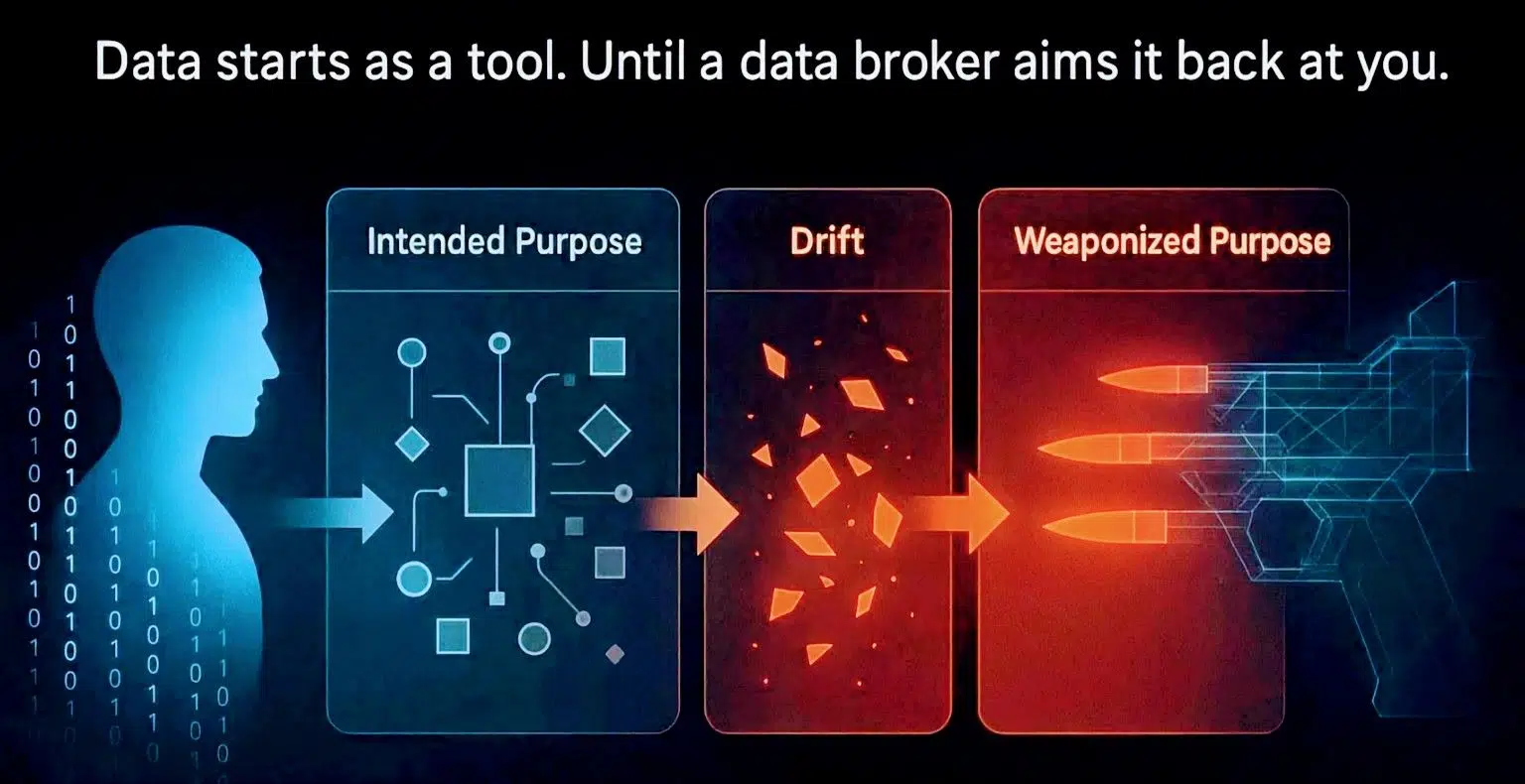
Personal data is a tool. Until a data broker aims it back at you.
We share data every day. For safety, connection, personalization, or convenience.
Each act feels harmless. It serves a clear purpose. But behind the surface, that same information is often reused, resold, or redirected toward a different goal. One that rarely benefits us.
This is what we call Weaponized Purpose.
A dataset begins life as a tool. It’s collected with good intent: to protect, to optimize, to improve. Over time, that purpose mutates. Incentives shift. What started as helpful becomes infrastructure for control, persuasion, or surveillance.
At ObscureIQ, we mapped twelve core categories of personal data to show how this transformation happens. How every form of collection, no matter how legitimate, can be turned against the individual.
Understanding the Lifecycle
Every dataset passes through three stages:
- Intended Purpose: the reason it was collected.
- Weaponized Purpose: how it’s later exploited or repurposed.
- Impact: what that shift means for privacy, autonomy, or safety.
“Purpose is the origin story of data. Weaponization is its sequel.”
 Marketing & Profiling :: The Predictability Industry
Marketing & Profiling :: The Predictability Industry
Intended Purpose: Personalization and customer engagement.
Weaponized Purpose: Profiling, behavioral prediction, political targeting.
Ad-tech promised relevance. What it built was surveillance.
Data brokers like LiveRamp, Acxiom, and Oracle construct massive identity graphs linking browsing habits, purchase history, and inferred beliefs.
When these datasets are reused for influence campaigns, personalization turns into manipulation.
Impact: Consumer data becomes a lever for shaping perception. And consent collapses under automation.
Did you know? Over 70% of U.S. web traffic passes through ad-tech trackers tied to fewer than ten major data brokers.
 Social & Expressive :: When Expression Becomes Evidence
Social & Expressive :: When Expression Becomes Evidence
Intended Purpose: Communication, community, and connection.
Weaponized Purpose: OSINT mining, reputation scoring, predictive social analysis.
Public expression used to mean visibility. Now it means vulnerability.
Companies like Babel Street and ZeroFox convert tweets, posts, and livestreams into behavioral intelligence.
What you say becomes a signal of who you are. And who you might become.
Impact: Speech becomes searchable, and every opinion is archived for targeting.
“Free expression is now a data feed.”
 Health & Biometric :: The Body as a Dataset
Health & Biometric :: The Body as a Dataset
Intended Purpose: Wellness, diagnosis, and innovation.
Weaponized Purpose: Genetic monetization, insurer risk modeling, targeted advertising.
Health data is among the most sensitive — yet wearables and genomic platforms like 23andMe and IQVIA trade on it.
Once shared, biological data is nearly impossible to retract.
Impact: Your health history becomes a permanent identifier that can’t be changed.
Did you know? The average fitness tracker records 100,000+ data points per day. Enough to infer location, stress, and sleep patterns.
 Location & Mobility :: The Geography of Exposure
Location & Mobility :: The Geography of Exposure
Intended Purpose: Navigation, convenience, safety.
Weaponized Purpose: Movement tracking, geofencing, law enforcement surveillance.
Every trip leaves a trail.
Companies like Verra Mobility, Arity, and Cuebiq sell movement data to insurers, marketers, and investigators.
Even “anonymized” datasets can re-identify individuals within hours.
Impact: Where you go becomes who you are — and who can find you.
Learn more: Be Location Safe
“Location is identity — it only needs a map.”
 Financial & Transactional :: Economic Surveillance Systems
Financial & Transactional :: Economic Surveillance Systems
Intended Purpose: Credit scoring, fraud prevention, transparency.
Weaponized Purpose: Behavioral scoring, predictive risk profiling, social credit overlays.
Financial data is supposed to measure solvency. Now it measures trustworthiness.
Credit bureaus like Equifax and Experian, and blockchain analytics firms like Chainalysis, analyze not just what you owe, but what you imply about your future behavior.
Impact: Economic records evolve into predictive judgment systems.
Related: Credit Headers: The Unseen Data Firehose
Did you know? Credit bureaus hold more than 1 billion active consumer profiles. Many containing behavioral scores invisible to the individuals they track.
 Identity & Access :: Authentication Becomes Observation
Identity & Access :: Authentication Becomes Observation
Intended Purpose: Security and verification.
Weaponized Purpose: Centralized identity tracking, breach exploitation, cross-system profiling.
Tools like Okta, Trulioo, and Onfido authenticate users across services.
But shared credentials and reused identity layers create invisible linkages. One breach can cascade across entire ecosystems.
Impact: The more seamless identity becomes, the harder it is to stay private.
Protect yourself: Password Managers: Privacy, Anonymity, and Security
“Convenience is authentication’s Trojan horse.”
 Public Records :: Bureaucracy Without Boundaries
Public Records :: Bureaucracy Without Boundaries
Intended Purpose: Document property, licensing, and legal proceedings.
Weaponized Purpose: Aggregated into people-search and skip-trace databases.
Public doesn’t mean permission.
Brokers like TruthFinder and BeenVerified scrape and sell court filings, deeds, and licensing data. Reconstructing private lives from public paperwork.
Impact: Routine legal records become a roadmap for harassment and fraud.
Learn how to fight back: Remove Residential Data
Did you know? Some people-search engines claim to refresh over 20 million court records per week.
 Civic Transparency :: When Openness Exposes Participants
Civic Transparency :: When Openness Exposes Participants
Intended Purpose: Promote accountability and democratic transparency.
Weaponized Purpose: Political microtargeting, harassment, and adversarial research.
Voter rolls, donor lists, and nonprofit directories were designed for oversight.
Platforms like ZoomInfo and PeopleDataLabs repackage them for corporate prospecting and political targeting.
Impact: Data meant to keep power accountable now puts citizens in the crosshairs.
“Transparency for systems. Exposure for people.”
 Research & Policy :: The Re-Identification Problem
Research & Policy :: The Re-Identification Problem
Intended Purpose: Study populations and improve outcomes.
Weaponized Purpose: Reuse and re-identification of anonymized datasets.
Research data once served public good.
Now, entities like LexisNexis Risk Solutions and Experian DataLabs merge it with commercial intelligence. Stripping away anonymity and selling insights.
Example: In 2023, researchers re-identified U.S. census data meant to be anonymous using commercial credit datasets proving that de-identification is a temporary illusion.
Impact: Population data gathered for social progress becomes private intelligence for profit.
Surveillance :: The Infrastructure of Control
Intended Purpose: Safety, security, law enforcement efficiency.
Weaponized Purpose: Predictive policing, population tracking, and commercial surveillance.
Systems from Flock Safety, Motorola Solutions, and Rekor capture millions of license plates daily.
These networks don’t forget. And they increasingly operate outside judicial oversight.
Impact: Safety tools evolve into the architecture of control.
Deep dive: ALPR vs. GPS: Why License Plate Tracking Is Surging | Opinion: Flock Safety is Surveillance Sold as Safety
Did you know? A single ALPR camera can log 30,000+ plates per day, often shared with hundreds of agencies.
Sensor & Automation :: When Machines Become Witnesses
Intended Purpose: Optimize infrastructure and efficiency.
Weaponized Purpose: Hidden monitoring, data fusion, and predictive analytics.
From smart traffic lights to drones, automation systems gather constant telemetry.
Companies like Teralytics and Here Technologies integrate this data into models predicting population flow and behavior.
Example: Smart-city traffic systems in Los Angeles and London already license telemetry to data marketplaces for “urban insights,” not safety.
Impact: Every “smart” system becomes a sensor for someone else.
“The smarter the system, the less invisible you are.”
System Telemetry :: Data Exhaust as Intelligence
Intended Purpose: System diagnostics and performance analytics.
Weaponized Purpose: Cross-platform behavioral mapping and commercial intelligence.
Cloud providers like Palantir, Snowflake, and AWS Data Exchange aggregate backend logs once meant for maintenance.
Those logs now reveal patterns about users, transactions, and even real-world movements.
Impact: Even digital exhaust becomes fuel for intelligence.
Related reading: Lock Down Browsers. Wipe Employee Footprints. Win Breach Wars.
The Pattern: Purpose as a Vector
Across all twelve categories, one truth holds:
Data is collected for utility. Then it’s retained, recombined, and reused until it can be weaponized.
What starts as purpose ends as power.
Why Weaponization Persists
Because incentives reward it. Surveillance capitalism profits from prediction. Governments seek insight.
Every actor bends purpose toward their own advantage. Until every system learns to aim.
“Weaponization isn’t a breach of purpose. It’s the business model.”
How ObscureIQ Helps
At ObscureIQ, we trace these flows.
Our privacy audits and intelligence frameworks expose how personal data moves through brokers, vendors, and platforms. Showing where intent ends and exploitation begins.
Want to know how your data could be weaponized?
Request a Digital Footprint Audit at ObscureIQ.com.
Explore our protection services:
Digital Footprint Wipe
Bespoke Deletes
ThreatWatch
Protection for Organizations


 Marketing & Profiling :: The Predictability Industry
Marketing & Profiling :: The Predictability Industry Social & Expressive :: When Expression Becomes Evidence
Social & Expressive :: When Expression Becomes Evidence Health & Biometric :: The Body as a Dataset
Health & Biometric :: The Body as a Dataset Location & Mobility :: The Geography of Exposure
Location & Mobility :: The Geography of Exposure Financial & Transactional :: Economic Surveillance Systems
Financial & Transactional :: Economic Surveillance Systems Identity & Access :: Authentication Becomes Observation
Identity & Access :: Authentication Becomes Observation Public Records :: Bureaucracy Without Boundaries
Public Records :: Bureaucracy Without Boundaries Civic Transparency :: When Openness Exposes Participants
Civic Transparency :: When Openness Exposes Participants Research & Policy :: The Re-Identification Problem
Research & Policy :: The Re-Identification Problem

