We See Trouble Before It Reaches You
Threats don’t start as headlines. They start as chatter in places most people never see. Forums, fringe networks, encrypted leaks, and local social feeds By the time they’re obvious, it’s often too late to respond without damage.
ThreatWatch exists to close that gap.
We monitor across the full spectrum of your exposure (digital and physical) so you know what’s building, where it’s coming from, and what to do next.
Discover your hidden risks before attackers do.
Three Layers of Defense
Enhanced Social & News Monitoring
- Pattern, intent, and escalation risk identification
- Social, public web, and news monitoring with analyst review
- Custom threat tags to reduce noise
- Covers names, aliases, orgs, events, addresses, IDs & leaked creds
Chatter Intelligence from the Dark Corners
- Monitors dark web, alt platforms & encrypted leaks
- AI + human analysis to flag leaks or targeting
- Identifies what others miss
- Low-signal chatter logged for escalation tracking
Geo-Specific Surveillance
- Geofencing and lat/long targeting for area monitoring
- Local social and digital posts analyzed
- Identifies surveillance or threat signals
- Flags privacy risks from unauthorized images or event leaks
What We Watch
- Names, aliases, usernames.
- Known addresses and event locations.
- Organization, brand, and domain mentions.
- Leaked credentials, account fragments, crypto wallets.
- Industry-specific triggers and high-risk keywords.

Service Tiers
ThreatWatchCORE
- Continuous, discreet monitoring across all three intelligence layers
- Daily analyst review of alerts
- Immediate notification for credible threats
- Weekly roll-up with exposure trends and visibility risk shifts
ThreatWatchRESPONSE
- All Core features
- Monitoring with analyst-led triage and recommendations
- Analyst-led validation of threat signals to cut false positives
- Written threat brief with severity rating and countermeasures
ThreatWatchCOMMAND-OPS
- All Response features
- Real-time alerting for imminent or high-severity threats
- Analyst access for live consultation during incidents
- Liaison support for takedowns, law enforcement, or PR containment
We protect the high-risk & high-profile with elite services.
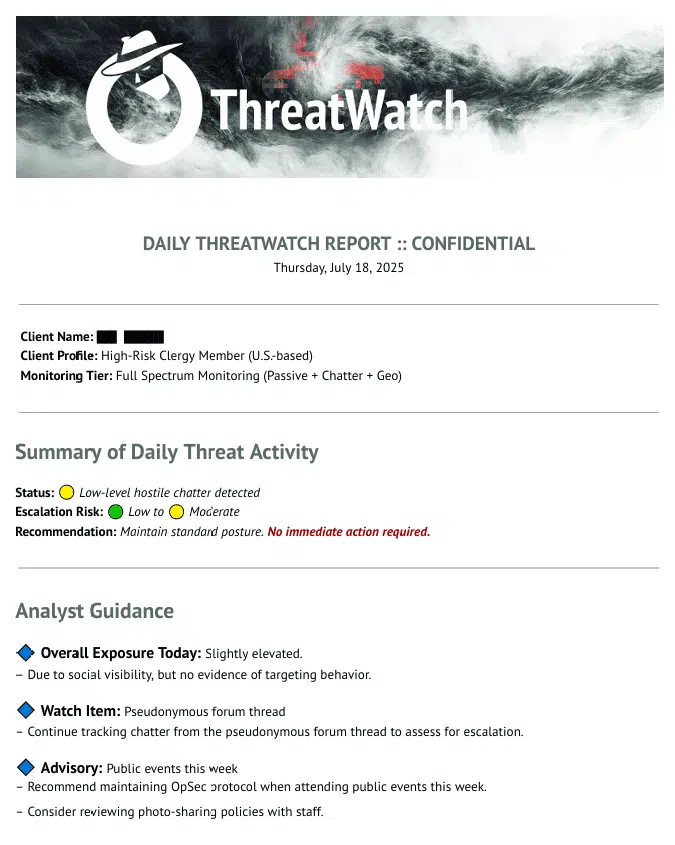
How It Looks in Practice
A recent daily report for a high-risk client:
- Hostile but low-level chatter on social media. No action required.
- Unverified mentions tied to a viral clip. Visibility risk elevated.
- Fringe forum post naming client. No coordinates or physical threat attached.
- Privacy risk from unblurred images of minors at a public event posted in a semi-private group.
Every finding reviewed by our analysts. Every risk given context and next steps.
Extend Your ThreatWatch Coverage
ThreatWatch can scale to match your threat environment. Add-ons expand coverage, deepen analysis, and target protection where it matters most.
People & Location Coverage
- Priority Monitoring for a Family Member: Tailored alerts and focused analyst review.
- Dedicated Monitoring for a Location: Location-specific rules and geo intelligence.
Coverage Depth & Custom Logic
- Extra Identifiers: Add names, emails, or asset profiles.
- Custom Monitoring Logic: Tailored detection for unique threats or high-grade adversaries.
Analyst Support & Intelligence
- Adversary Attribution: Identify and profile threat actors.
- Emergency Takedown / Remediation: Rapid disruption of hostile content.
- Incident-Response Retainer: 24/7 analyst access when it matters most.
- On-Call Analyst Extension: Extra scanning, research, or custom task hours.
Travel & Event Security
- Pre-Travel Threat Monitoring: Scans ahead of high-profile trips.
- Event/Board Meeting Watch: Attendee & venue-based monitoring.
- Event-Specific Monitoring: Real-time digital perimeter defense.
Premium Support & Integration
- VIP Concierge Monitoring: White-glove analyst access & monitoring.
- Custom Secure Comms Setup: Encrypted communication channels.
- Software Integration: Link to SOC or internal ticketing systems.
Physical Security
- Physical Security Coordination: On-site protection by vetted professionals.
Secure Contact Request
We use encrypted channels and passive filtering. No tracking.
